Secure SSH-Agent Forwarding with SSH-Askpass
Forwarding your identity with SSH-Agent may lead to security nightmares, if the remote machine is compromised. Your key material will not leak, but an attacker with root access on the remote machine will be able to initiate ssh connections with your identity.
I tried to make my setup a bit more secure with the following approach on OSX 10.9.
The following script was saved as /usr/libexec/ssh-askpass and was
made executeable:
#! /bin/sh
#
# An SSH_ASKPASS command for MacOS X
# Based on script by Joseph Mocker, Sun Microsystems
# Save as /usr/libexec/ssh-askpass and chmod +x
TITLE=${MACOS_ASKPASS_TITLE:-"SSH Agent"}
DIALOG="display dialog \"$@\" buttons {\"Deny\", \"Allow\"} default button 2"
DIALOG="$DIALOG with title \"$TITLE\" with icon caution"
result=`osascript -e 'tell application "Terminal"' -e "$DIALOG" -e 'end tell'`
if [ "$result" = "button returned:Allow" ]; then
exit 0
else
exit 1
fi
Then I removed all keys from the ssh-agent. You can display all currently registered keys with:
ssh-add -l
Then remove all keys with:
ssh-add -D
And then re-add every key, specifiying that a confirmation is needed before it is used:
ssh-add -c /path/to/key_file
(The paths can be copied from the ssh-add -l output.)
Note: The last two steps need to be repeated after every reboot!
After performing these steps everytime I open an ssh connection (including connections originating at remote hosts using my local identity) I have to confirm a dialog like this one:
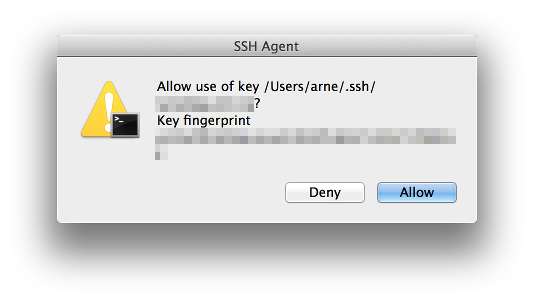
This way no one can use my forwarded identity to initiate connections without my knowledge.